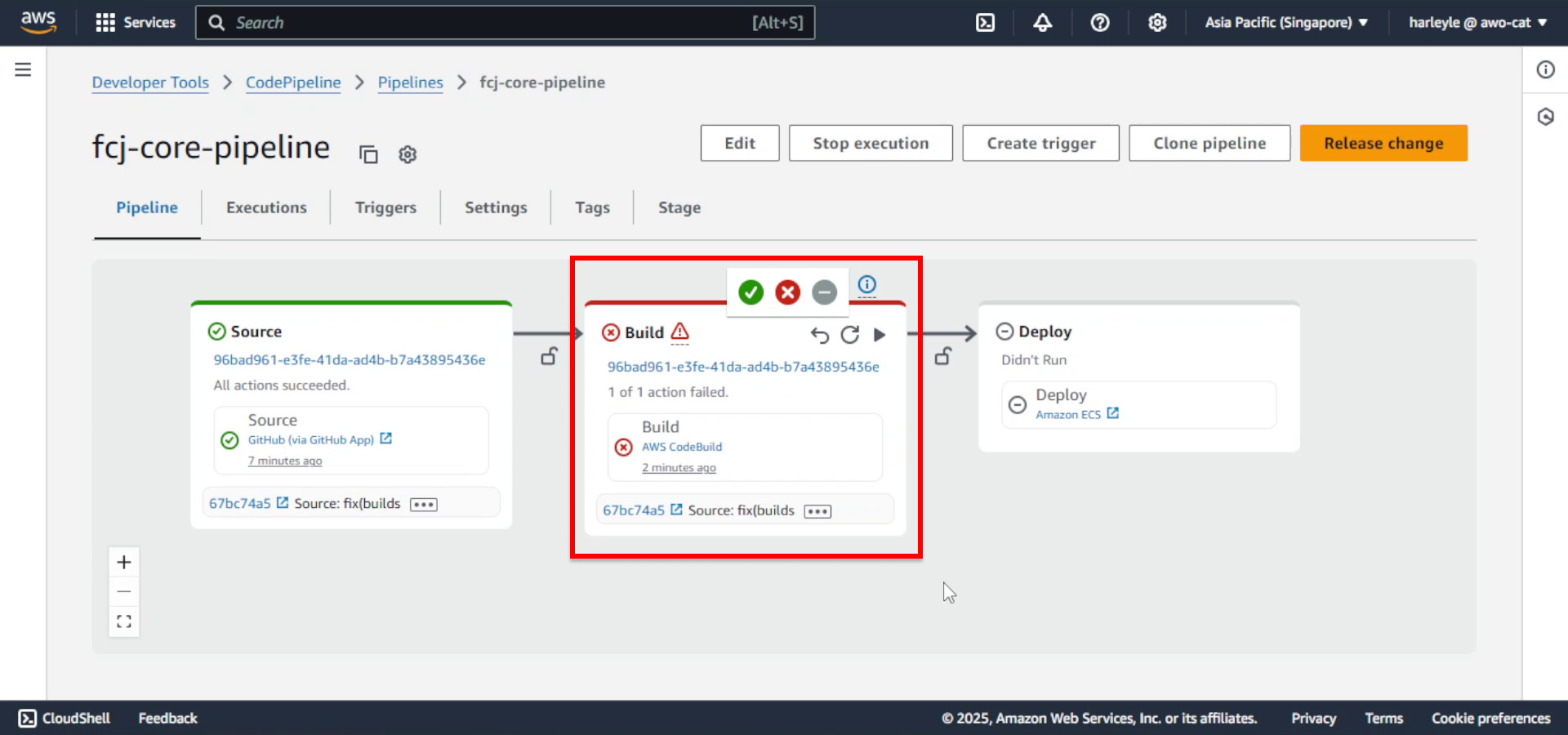
Create CI/CD Pipeline with AWS CodePipeline
Examine buildspec.yml
A buildspec is a collection of build commands and related settings, in YAML format, that AWS CodeBuild uses to run a build. You can include a buildspec file (typically named buildspec.yml) as part of your source code, or you can define the buildspec configuration directly when you create a build project. This workshop provides this file, so you don’t have to write it from scratch. Let’s examine its contents.
version: 0.2
env:
secrets-manager:
FLYWAY_URL: "dev/fcj/momentum:DB_CONNECTION_STRING"
phases:
pre_build:
commands:
# Display login message and AWS version info
- echo Logging in to Amazon ECR...
- aws --version
# Authenticate Docker with Amazon ECR using AWS CLI
- aws ecr get-login-password --region $AWS_DEFAULT_REGION | docker login --username AWS --password-stdin $AWS_ACCOUNT_ID.dkr.ecr.$AWS_DEFAULT_REGION.amazonaws.com
# Set the ECR repository URI for the Docker image
- REPOSITORY_URI=$AWS_ACCOUNT_ID.dkr.ecr.$AWS_DEFAULT_REGION.amazonaws.com/$REPOSITORY_NAME
# Extract first 7 characters of commit hash for image tagging
- COMMIT_HASH=$(echo $CODEBUILD_RESOLVED_SOURCE_VERSION | cut -c 1-7)
# Create unique image tag using commit hash
- IMAGE_TAG="core-$COMMIT_HASH"
# Change to application directory
- cd application/Momentum/
# Make Maven wrapper executable
- chmod +x mvnw
# Run database migration using Flyway
- ./mvnw flyway:migrate -Dflyway.url=$FLYWAY_URL
# Return to previous directory
- cd -
build:
commands:
# Log build start time
- echo Build started on `date`
- echo Building the Docker image...
# Build Docker image from the Momentum application directory
- docker build -t $REPOSITORY_URI:core application/Momentum/
# Tag the image with the commit-specific tag
- docker tag $REPOSITORY_URI:core $REPOSITORY_URI:$IMAGE_TAG
post_build:
commands:
# Log build completion time
- echo Build completed on `date`
- echo Pushing the Docker images...
# Push the tagged image to ECR repository
- docker push $REPOSITORY_URI:core
- docker push $REPOSITORY_URI:$IMAGE_TAG
# Create image definitions file for ECS deployment
- echo Writing image definitions file...
- printf '[{"name":"core","imageUri":"%s"}]' $REPOSITORY_URI:$IMAGE_TAG > imagedefinitions.json
# Specify the artifact file to be used by deployment pipeline
artifacts:
files: imagedefinitions.json
Secret Injection Mechanism
As demonstrated in the buildspec.yml file, secrets from AWS Secrets Manager are made available to AWS CodeBuild by explicitly referencing them under the env.secrets-manager section. When the build process starts, AWS CodeBuild automatically fetches and injects these specified secrets as environment variables. For this mechanism to function correctly, the IAM role assumed by AWS CodeBuild must be granted the necessary permissions to access the designated secrets in AWS Secrets Manager.
env:
secrets-manager:
FLYWAY_URL: "dev/fcj/momentum:DB_CONNECTION_STRING"
Create CI/CD Pipeline
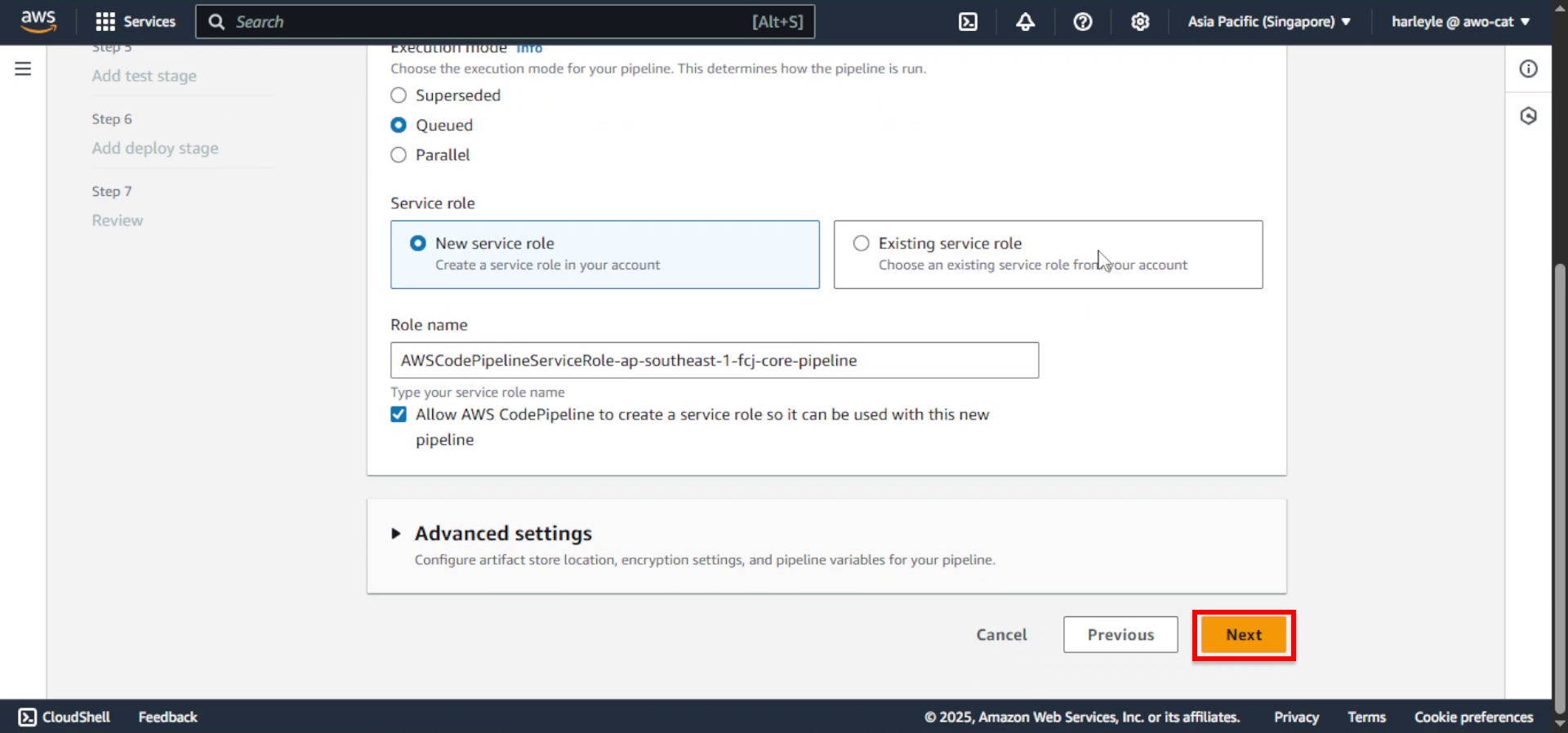
1. In the left navigation pane, under Pipeline - CodePipeline, select Pipelines. Click Create pipeline.
2. Select Build custom pipeline and click Next.
3. Configure pipeline settings:
- Pipeline name: Enter
fcj-core-pipeline
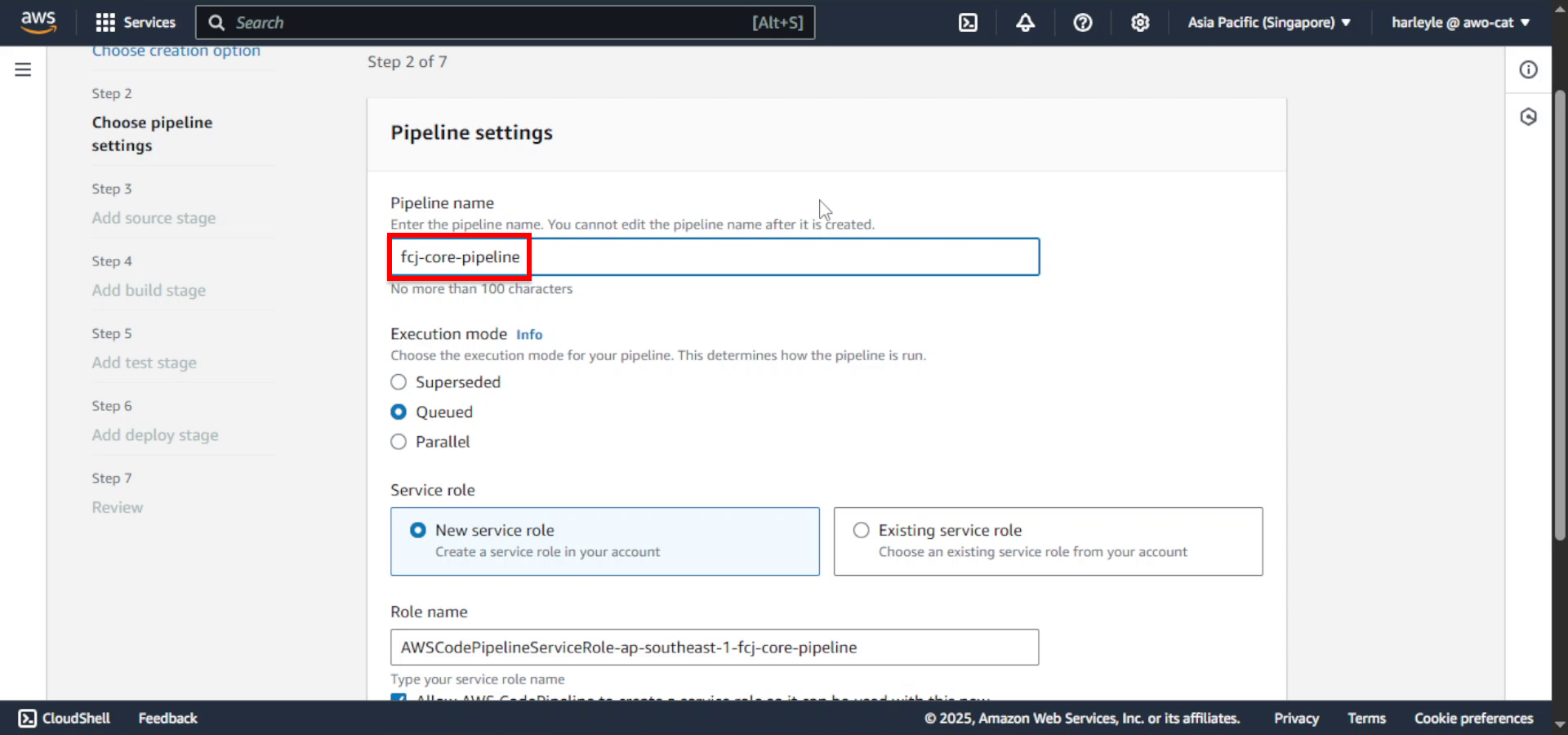
4. Click Next.
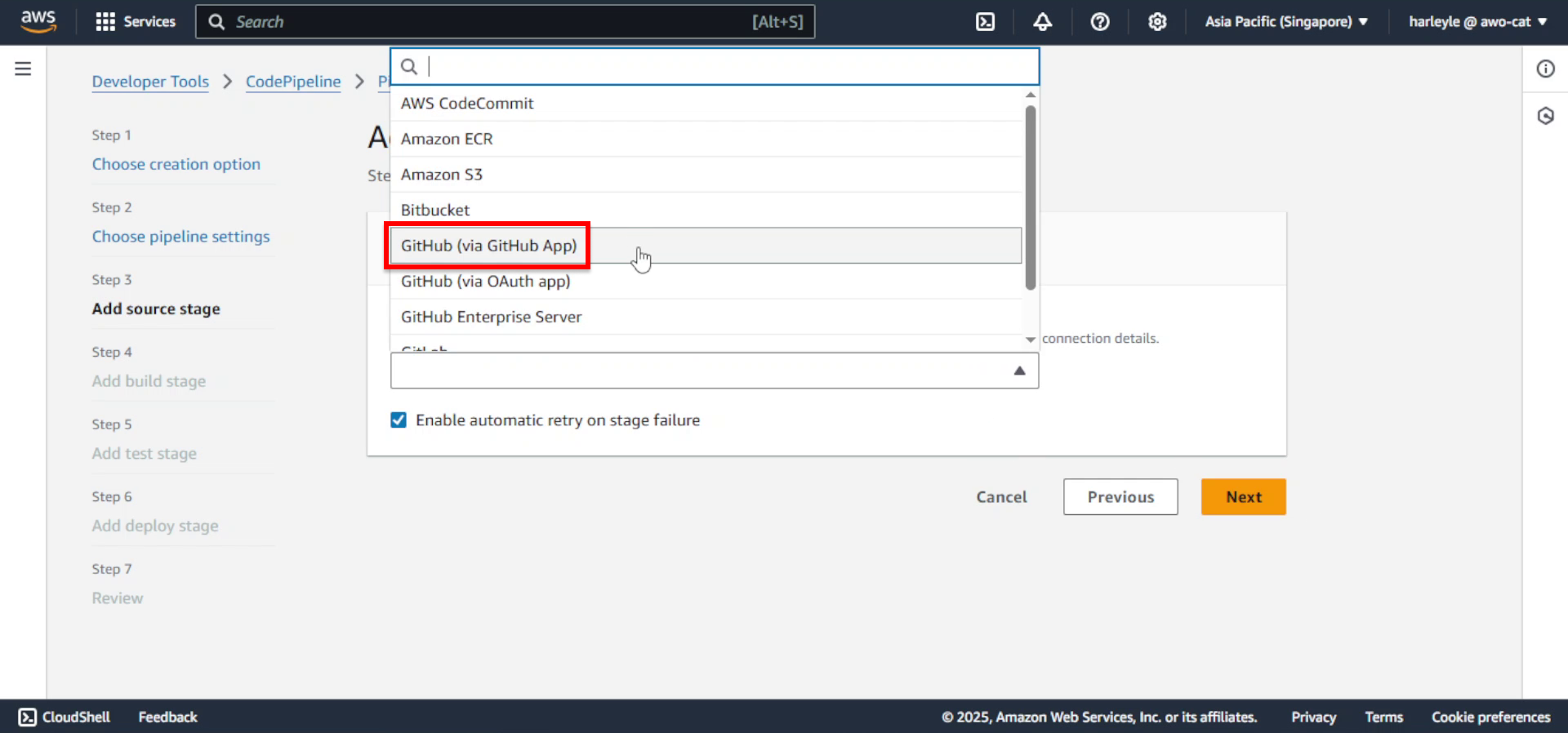
5. Configure the source stage:
- Source: Select GitHub (via GitHub App)
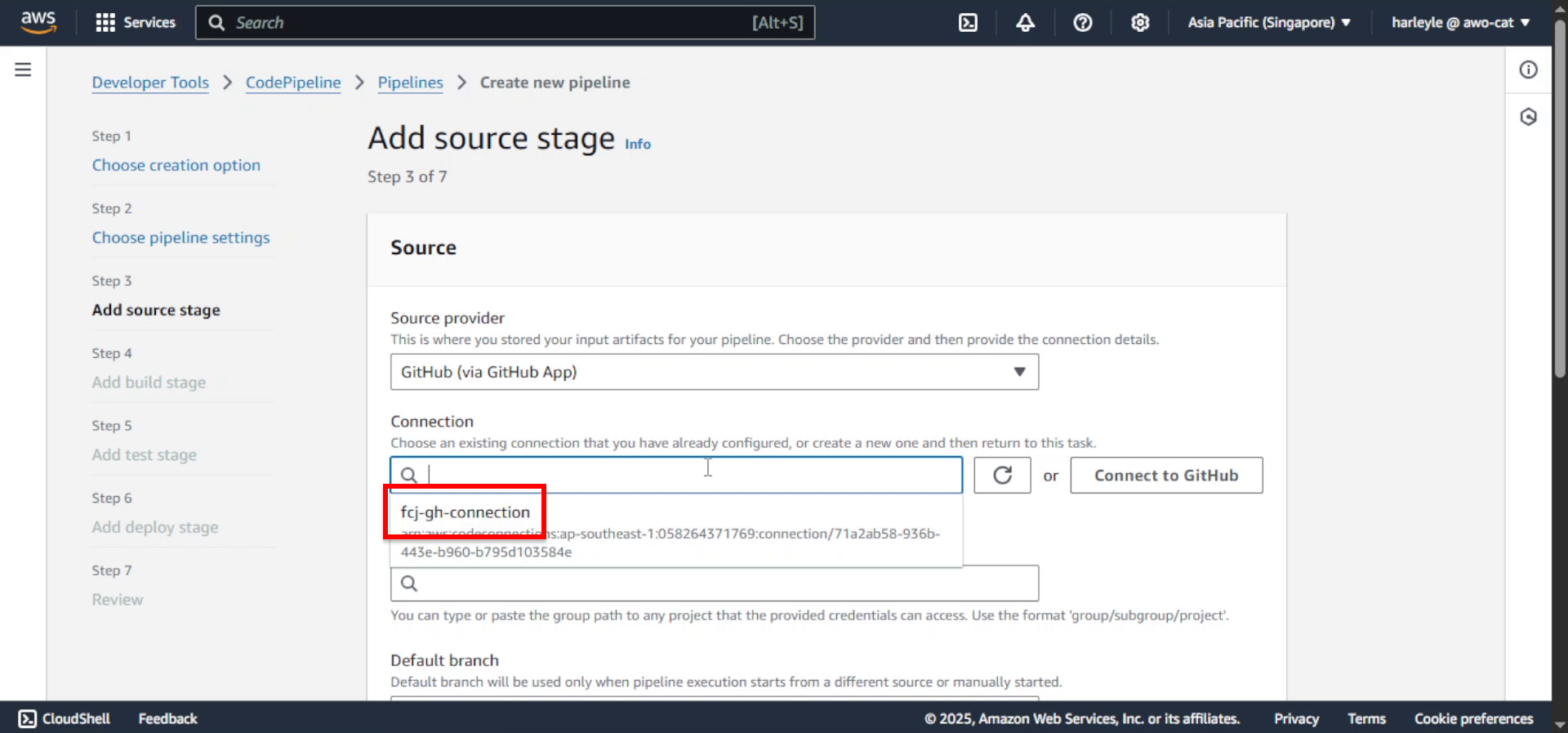
6. Configure connection settings:
- Connection: Select fcj-gh-connection
7. Select your forked repository.
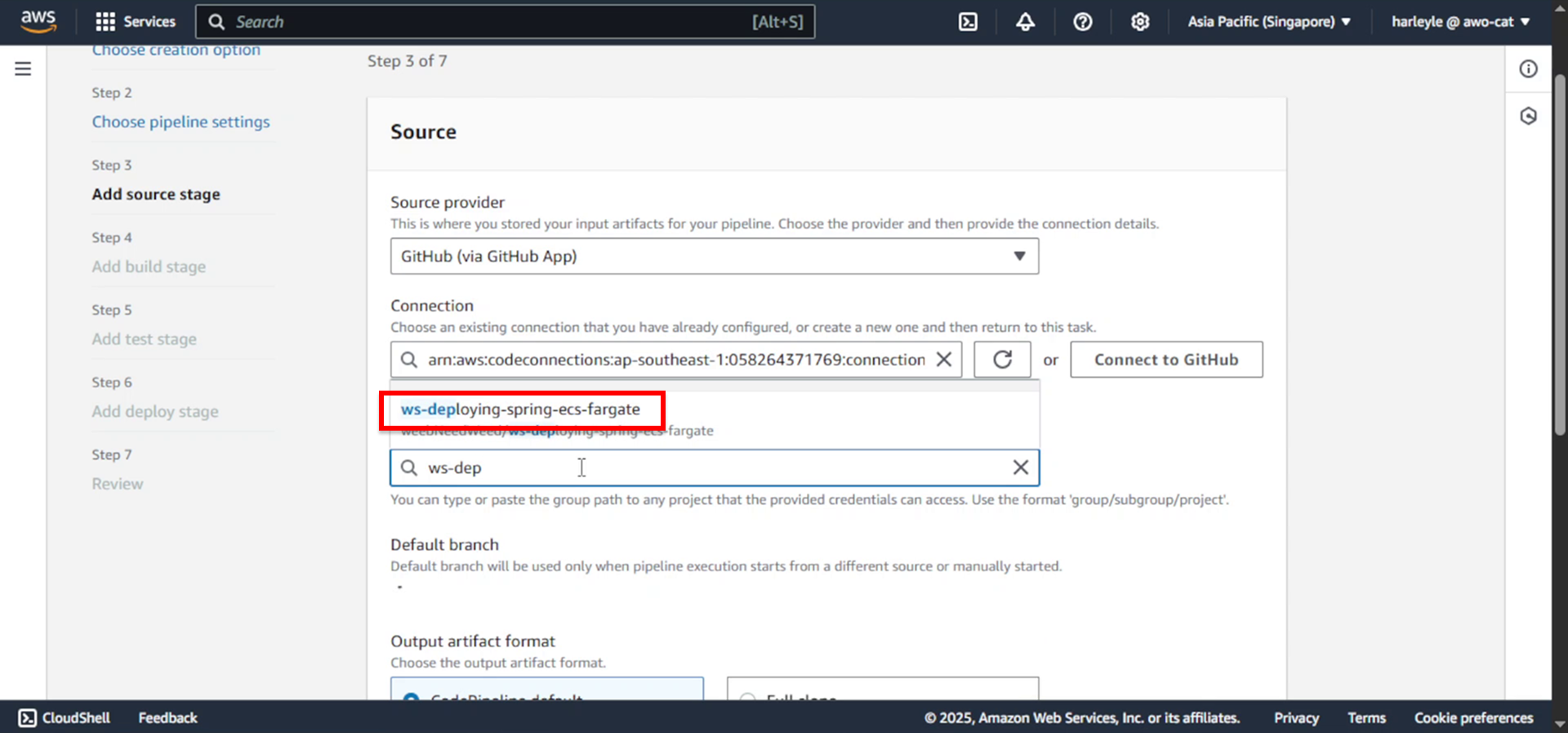
8. Configure branch settings:
- Default branch: Select master
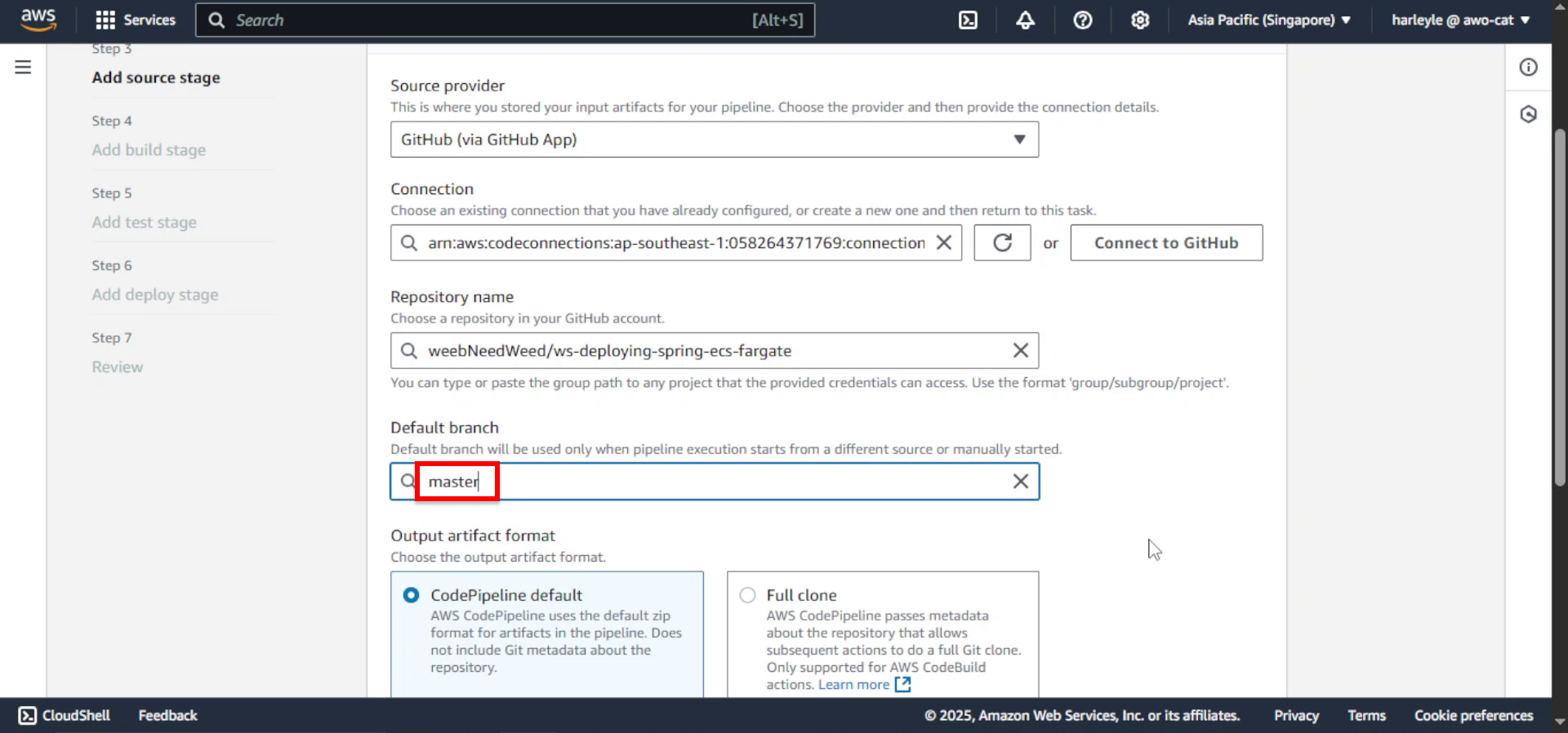
9. Click Next.
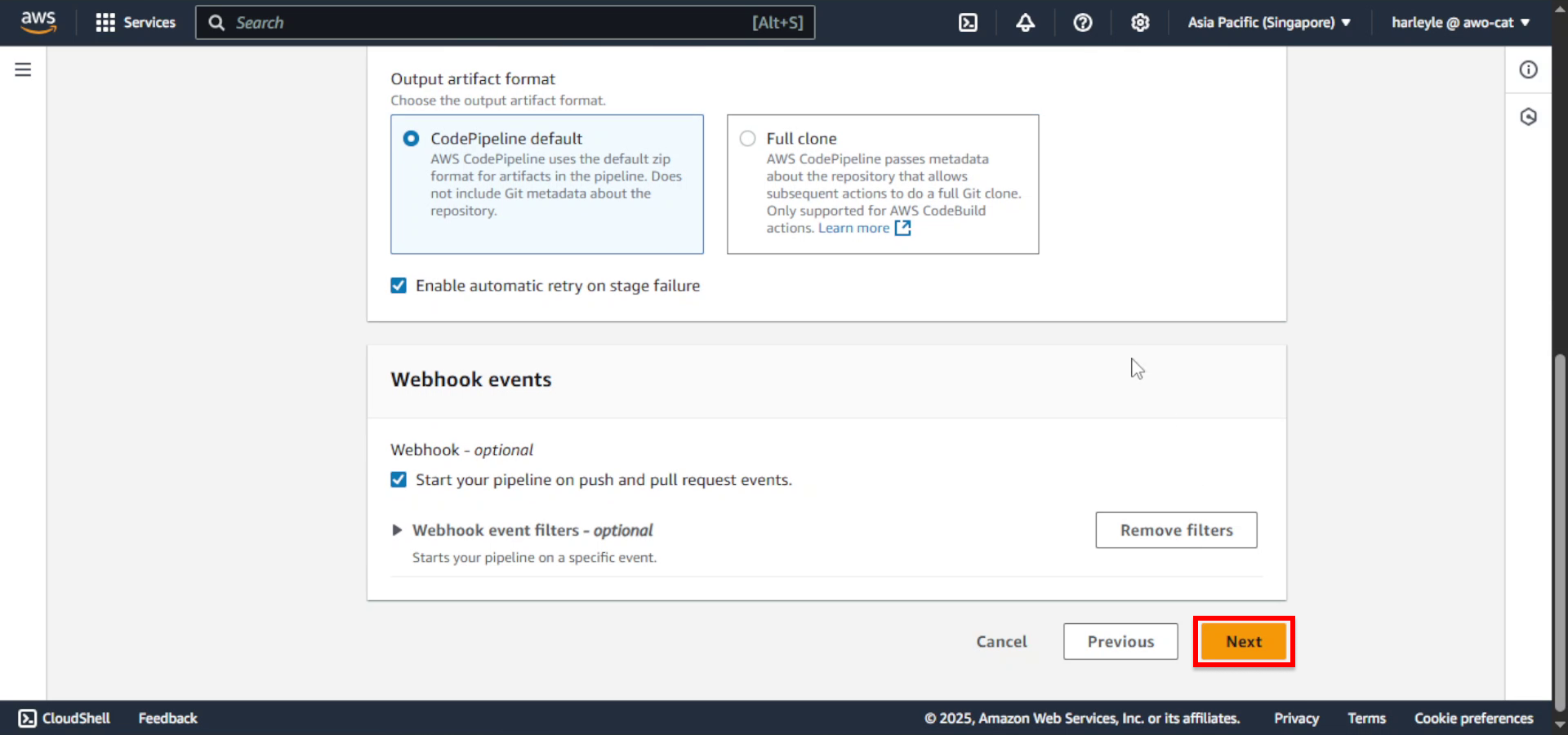
10. Configure the build stage: - Select Other build providers - Select AWS CodeBuild
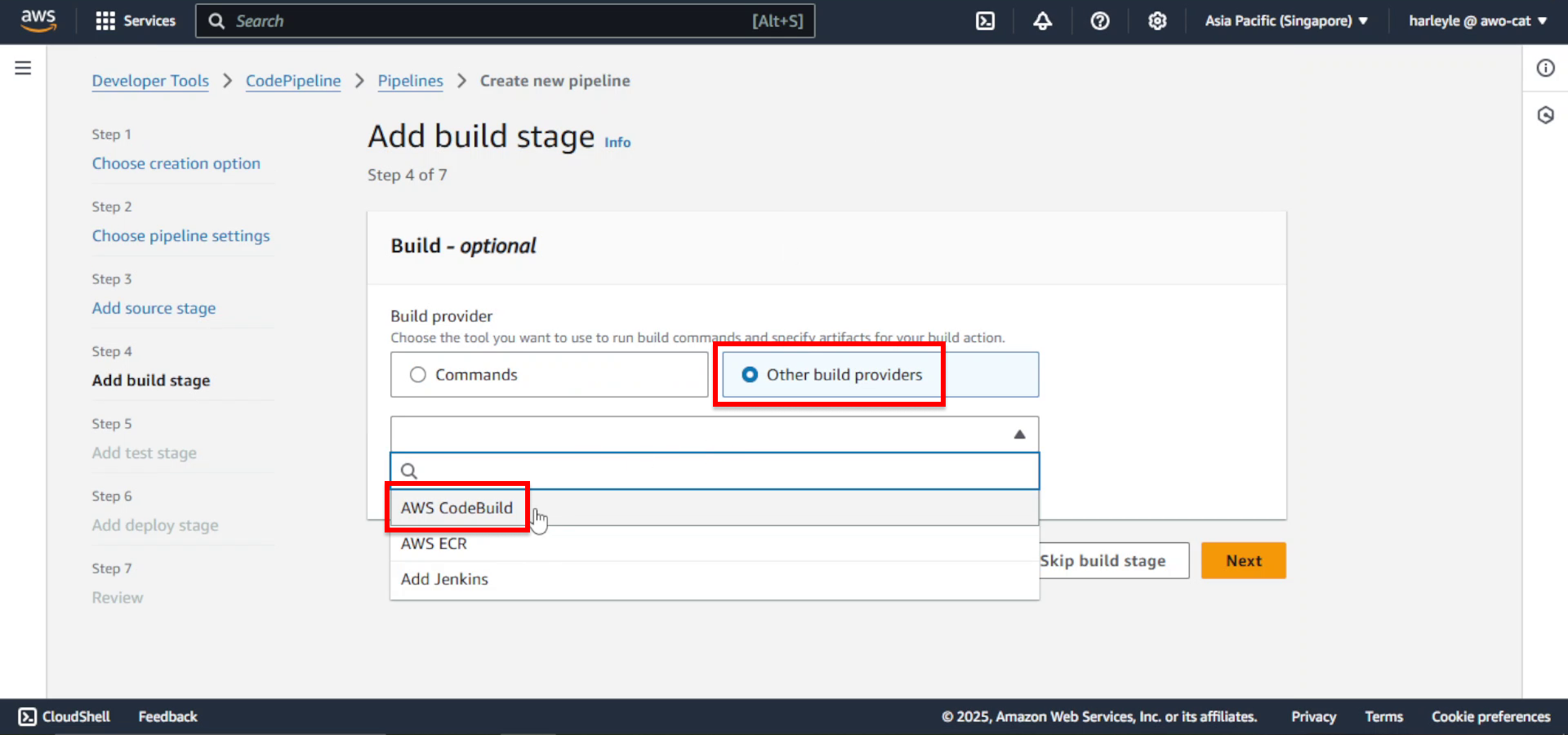
11. Click Create project. Another browser tab will open.
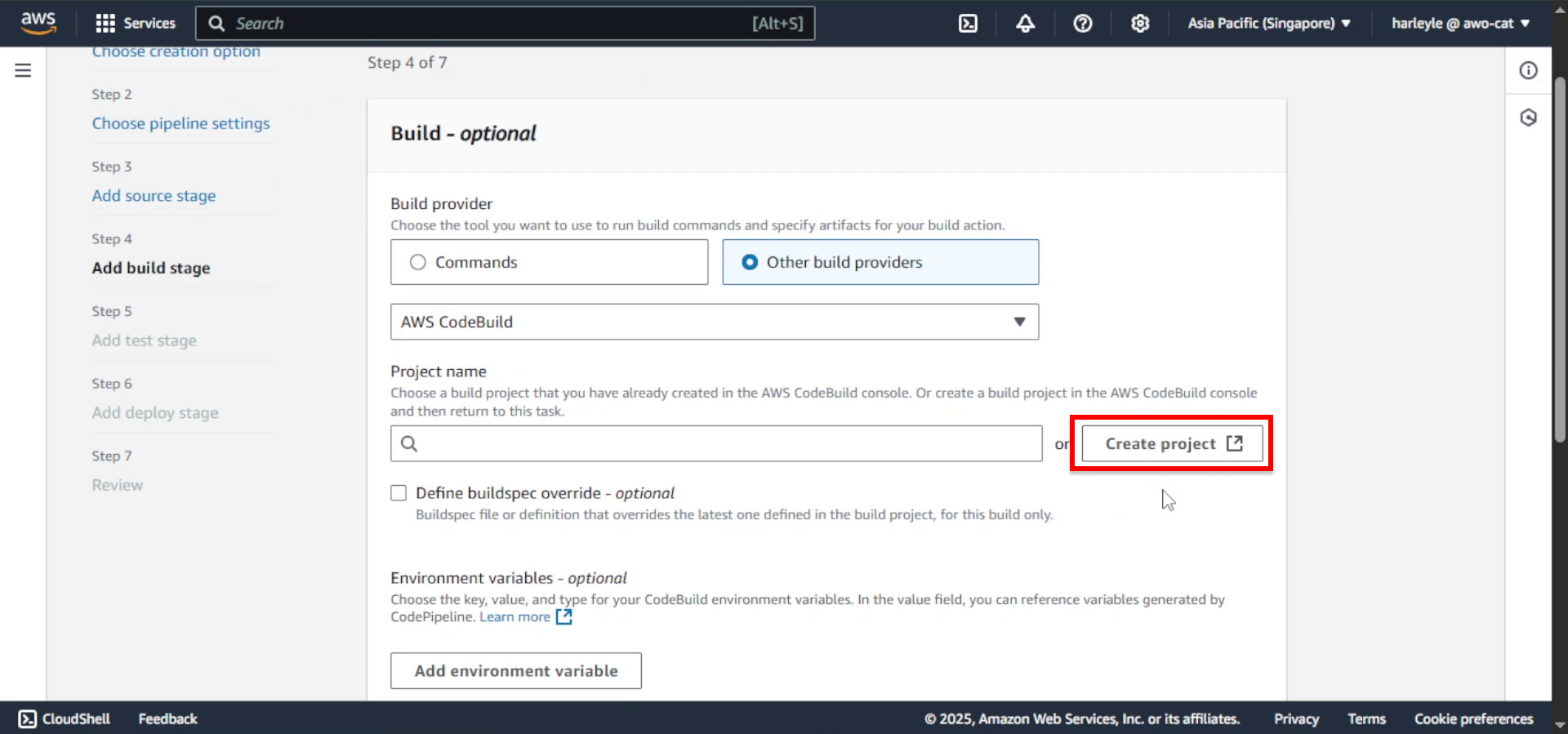
12. Configure project settings:
- Project name: Enter fcj-core-build
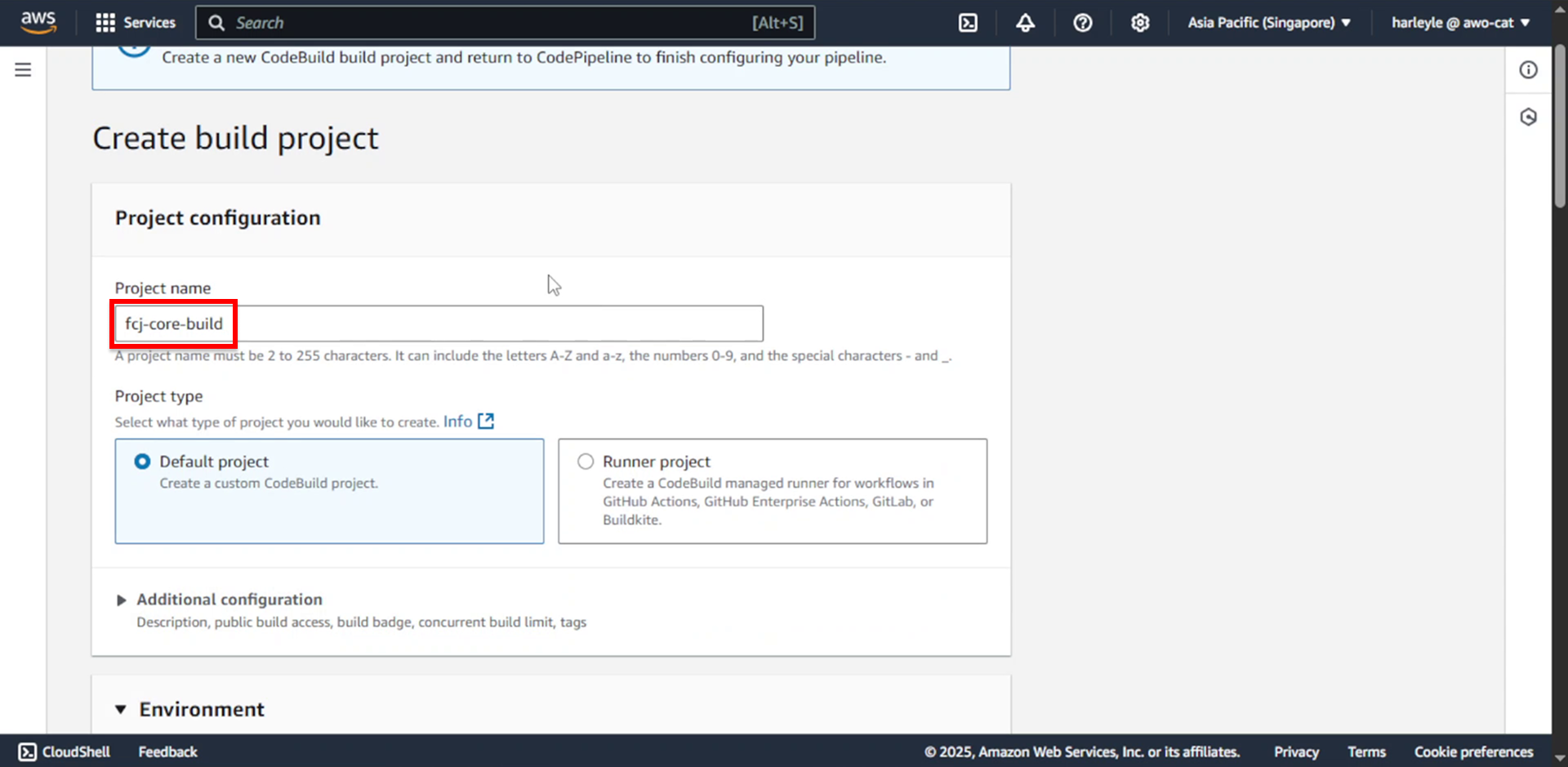
13. In the Environment section, expand Additional configuration.
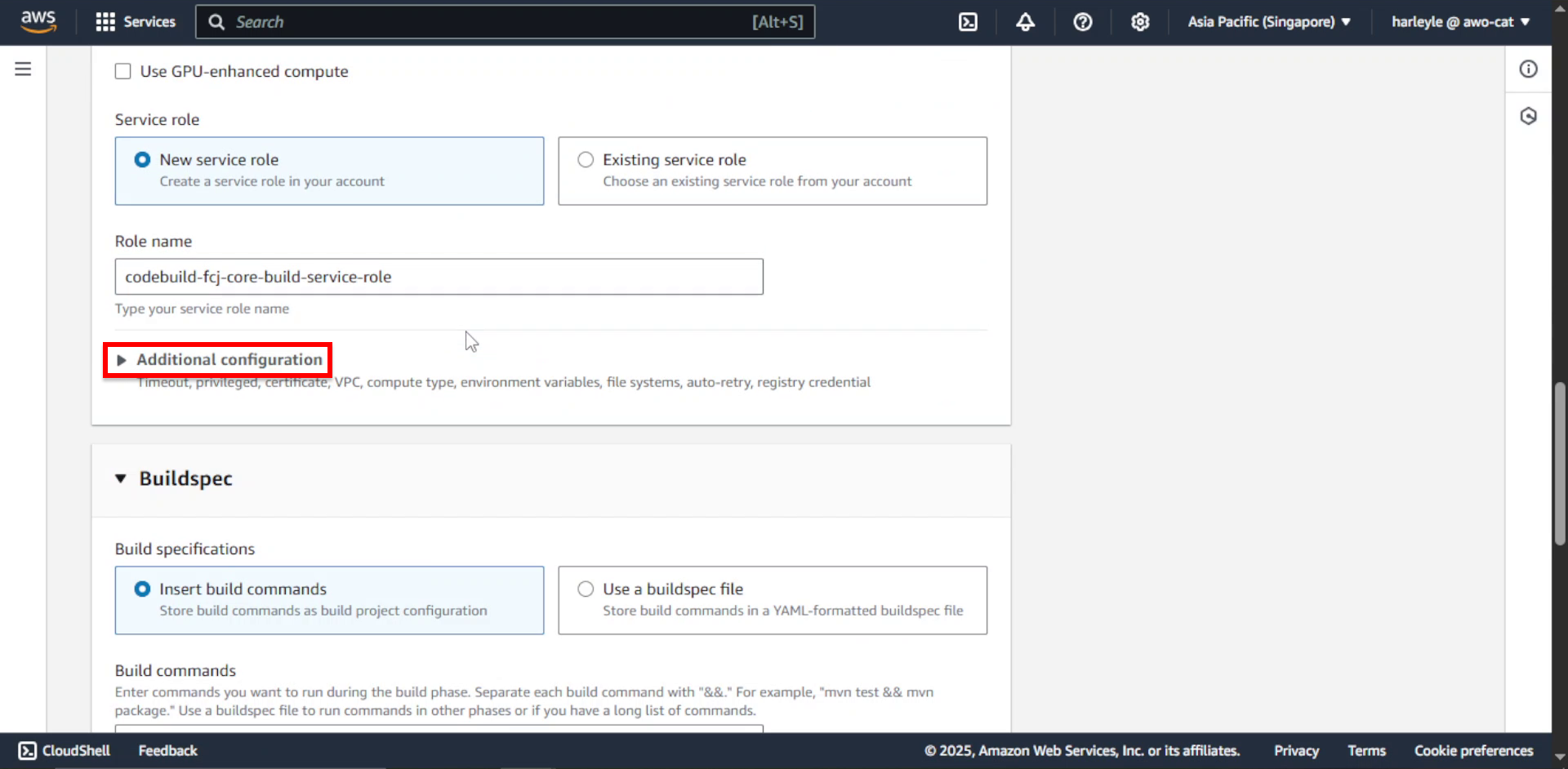
14. Check Enable this flag if you want to build Docker images or want your builds to get elevated privileges.
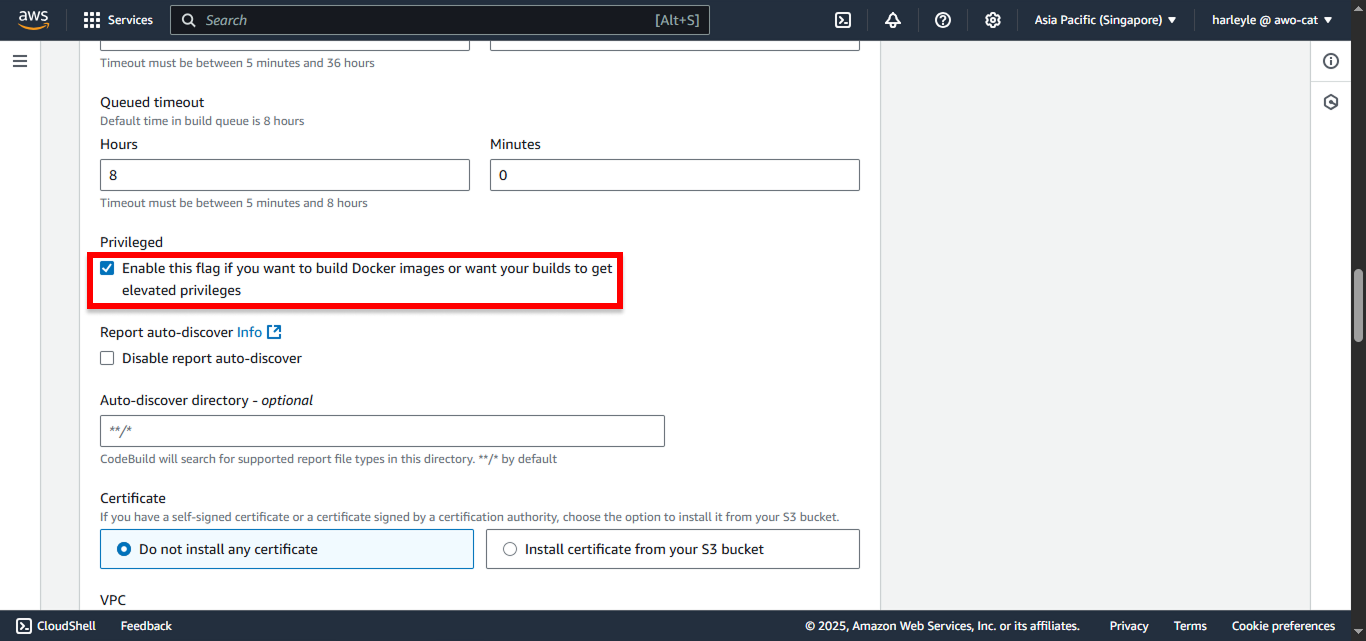
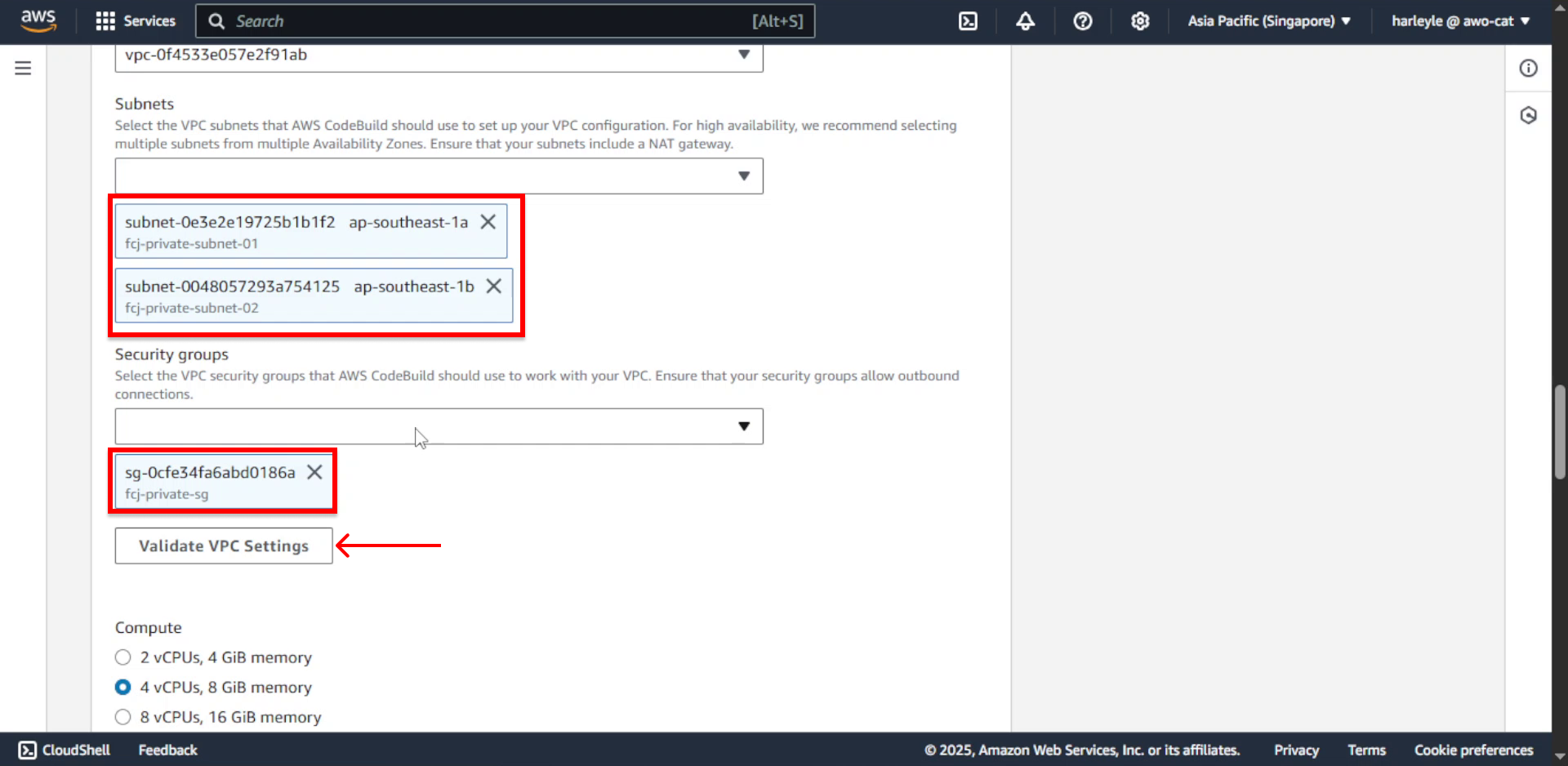
15. Configure VPC settings:
- VPC: Select fcj-vpc
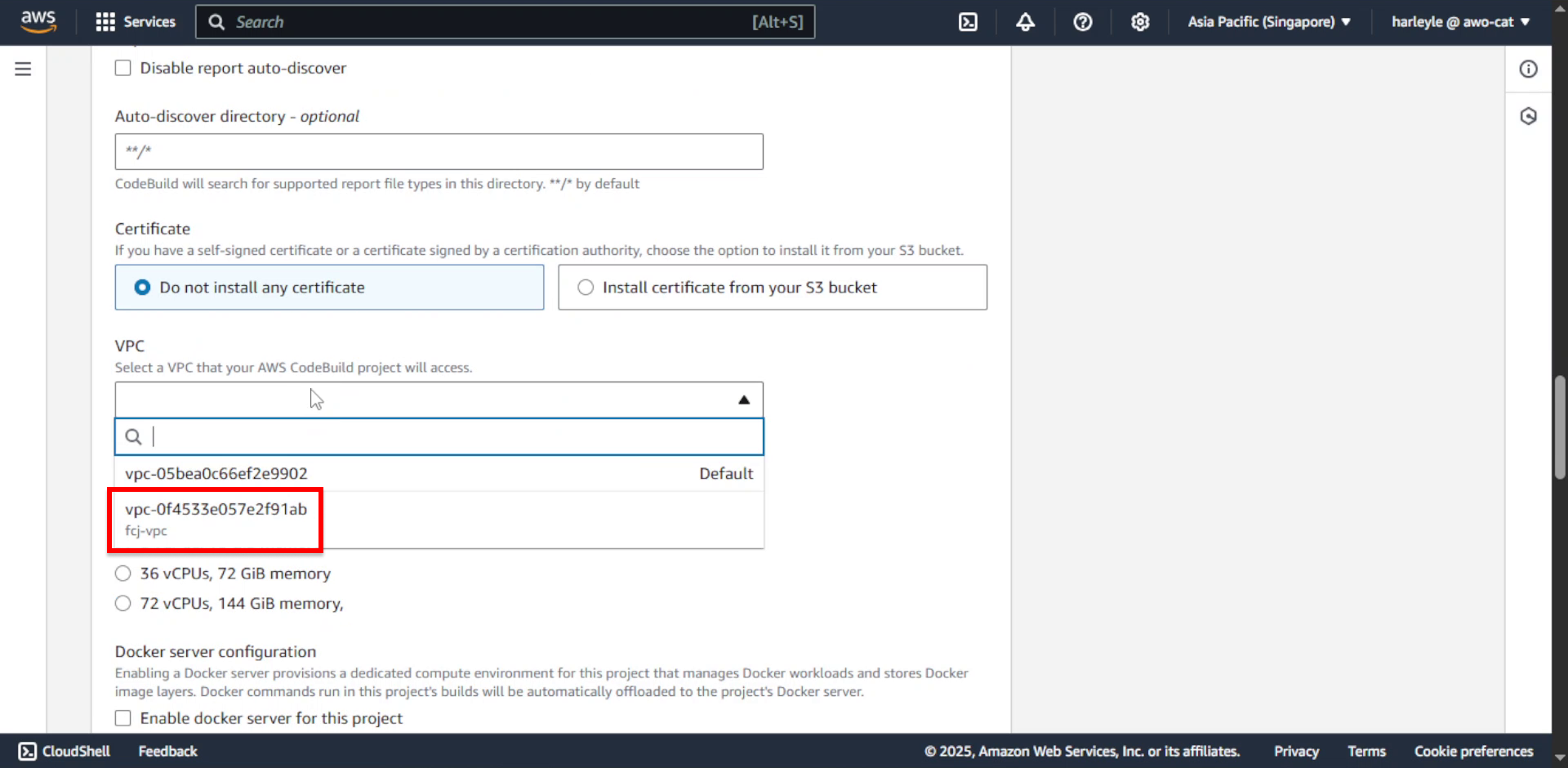
16. Configure network settings:
- Subnets: Select the two private subnets
- Security group: Select fcj-private-sg
- Click Validate VPC Settings to verify subnet connectivity
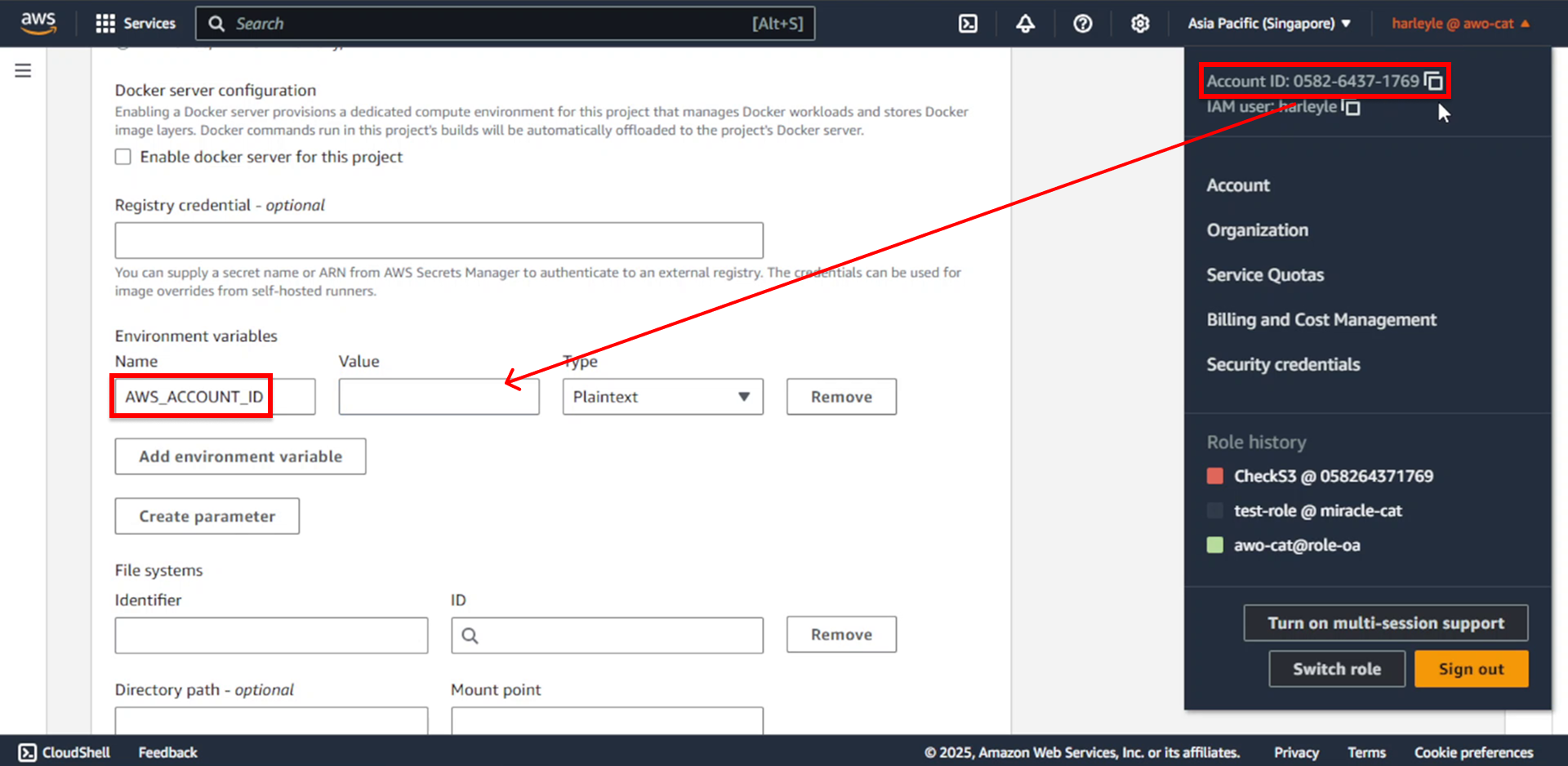
17. Configure environment variables:
- Name: Enter
AWS_ACCOUNT_ID - Value: Enter your AWS account ID
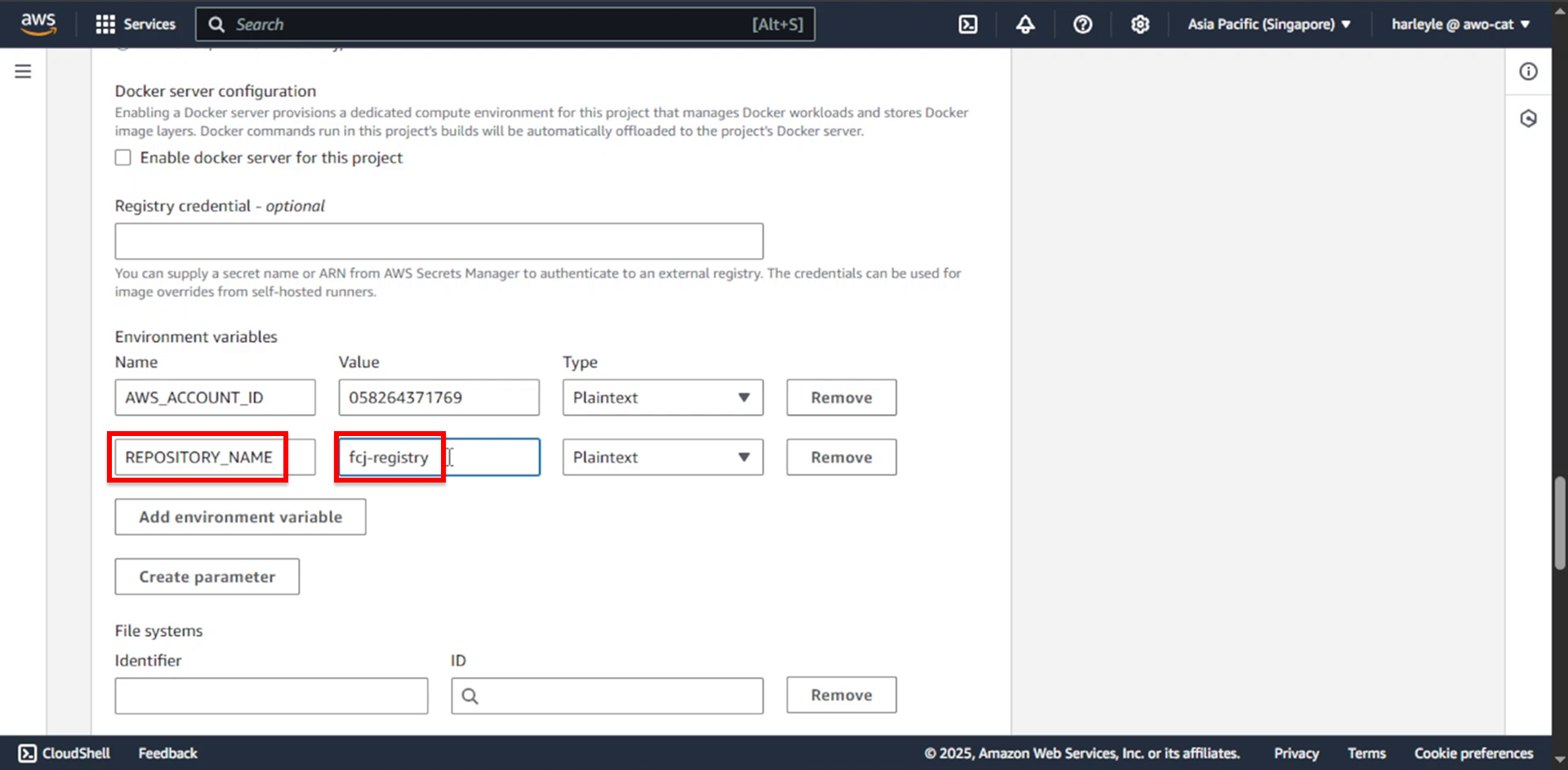
18. Add another environment variable:
- Name: Enter
REPOSITORY_NAME - Value: Enter
fcj-registry
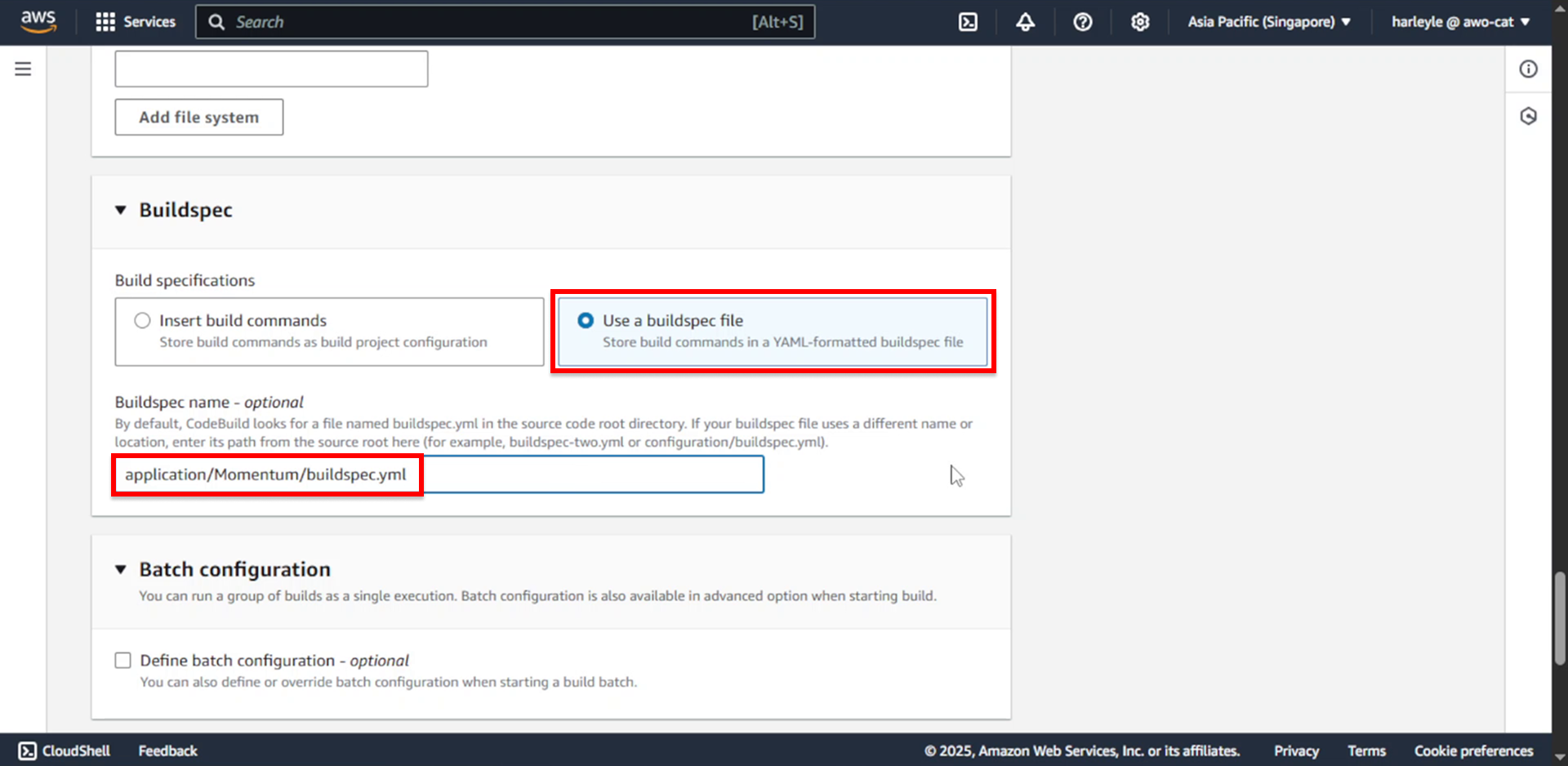
19. Configure buildspec settings:
- Select Use a buildspec file
- Buildspec name: Enter
application/Momentum/buildspec.yml
20. Scroll to the bottom and click Continue to CodePipeline.
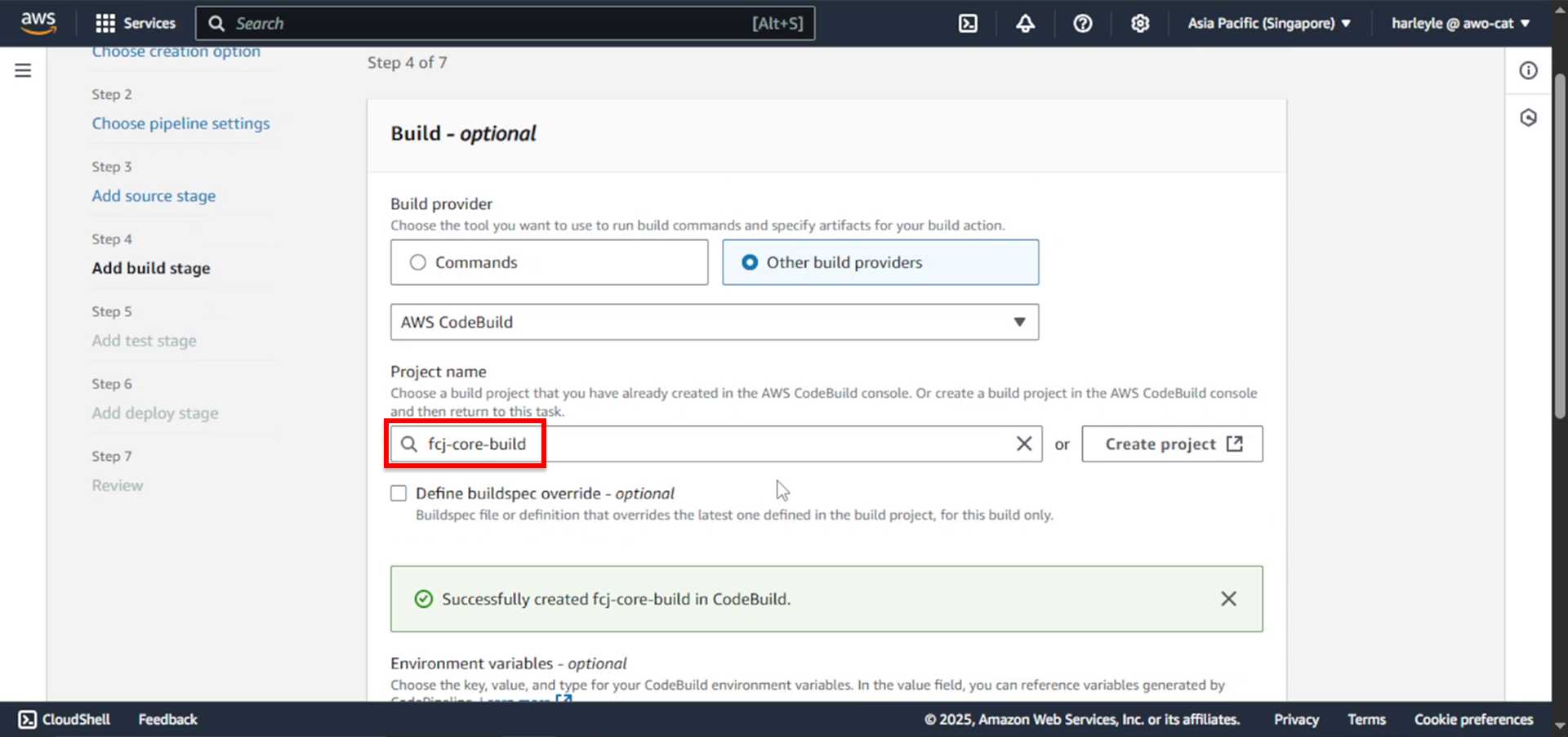
21. Verify that the fcj-core-build project is automatically selected.
22. Click Next.
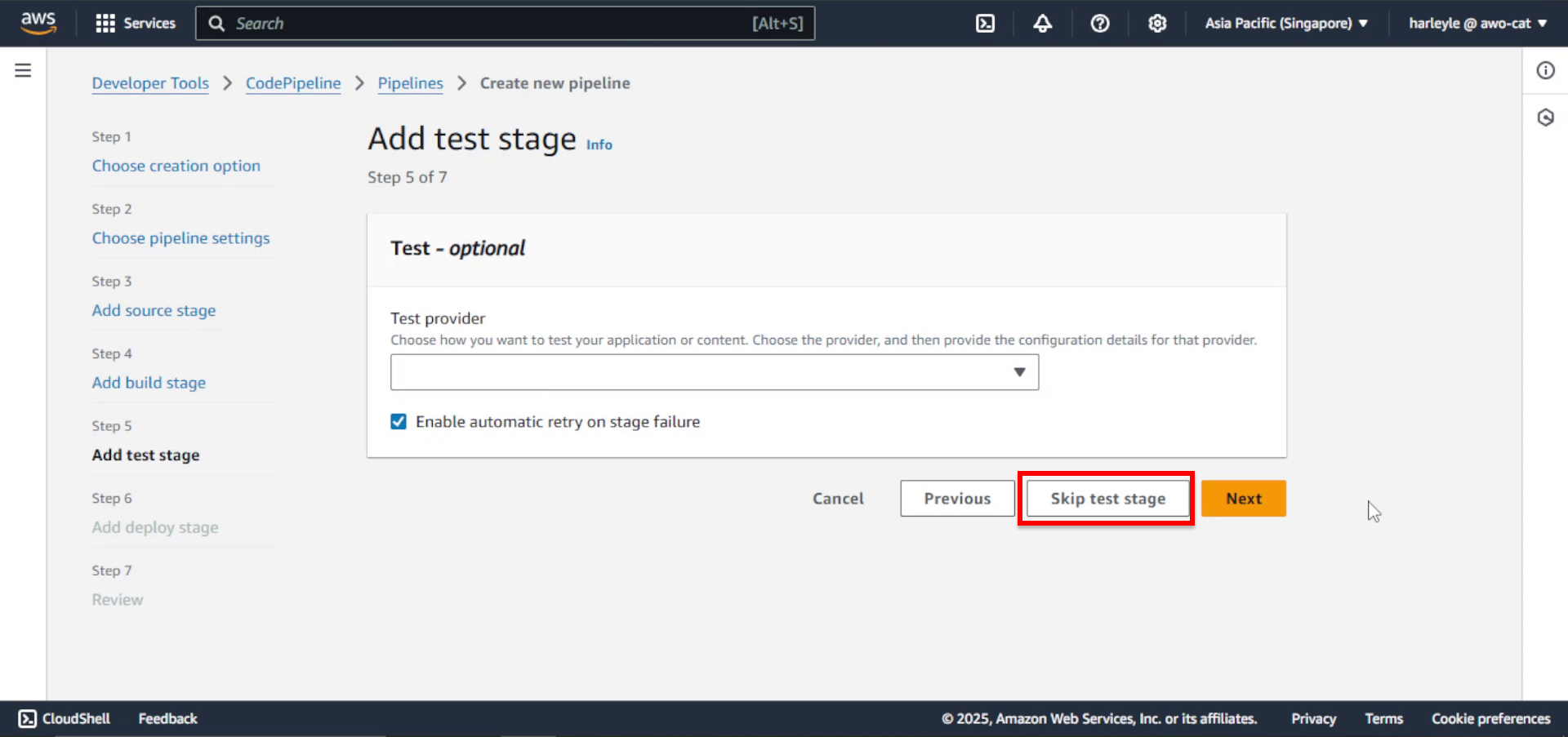
23. Skip the test stage by clicking Skip test stage.
24. Configure the deploy stage:
- Provider: Select Amazon ECS
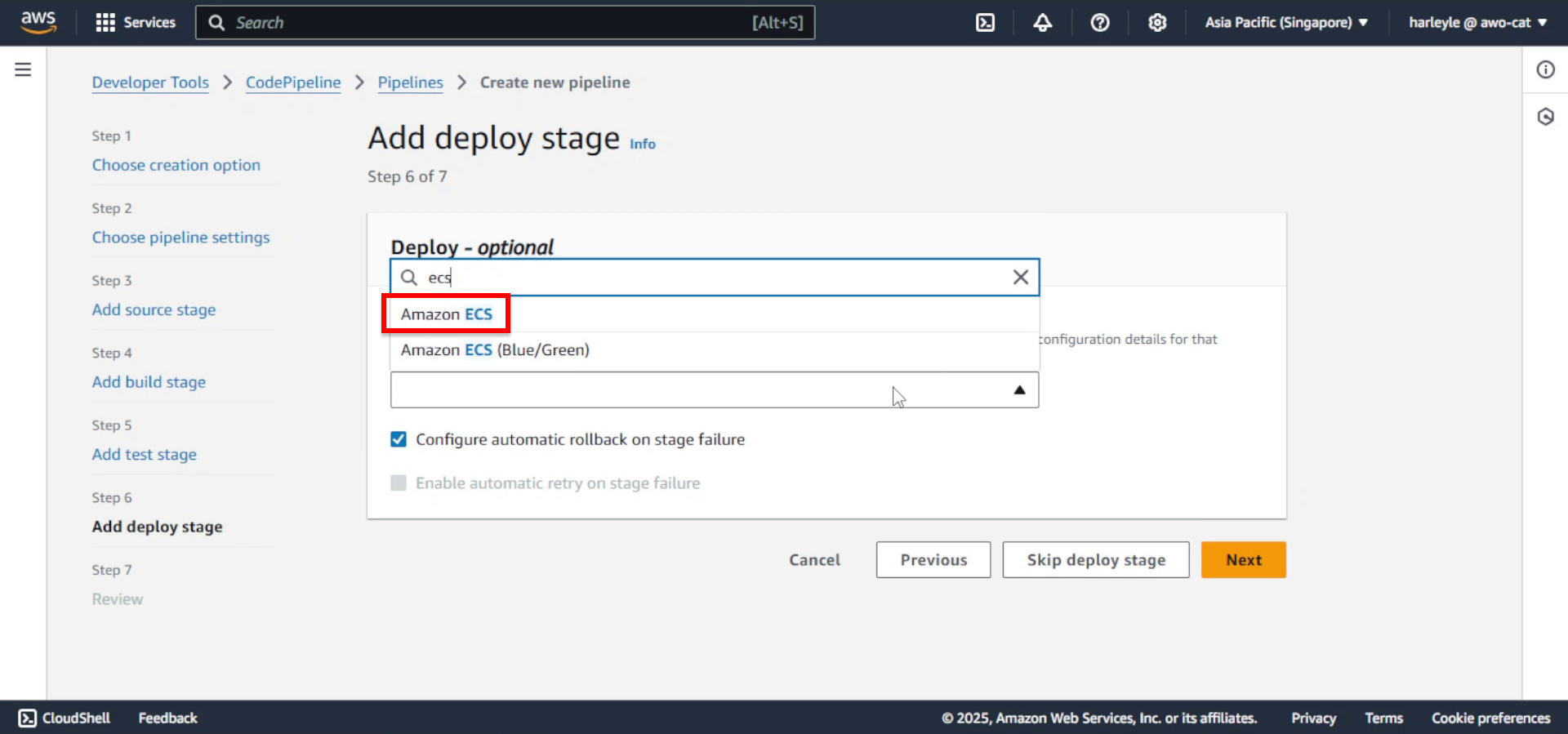
25. Configure deployment settings:
- Cluster name: Select fcj-ecs-cluster
- Service name: Select fcj-core-svc
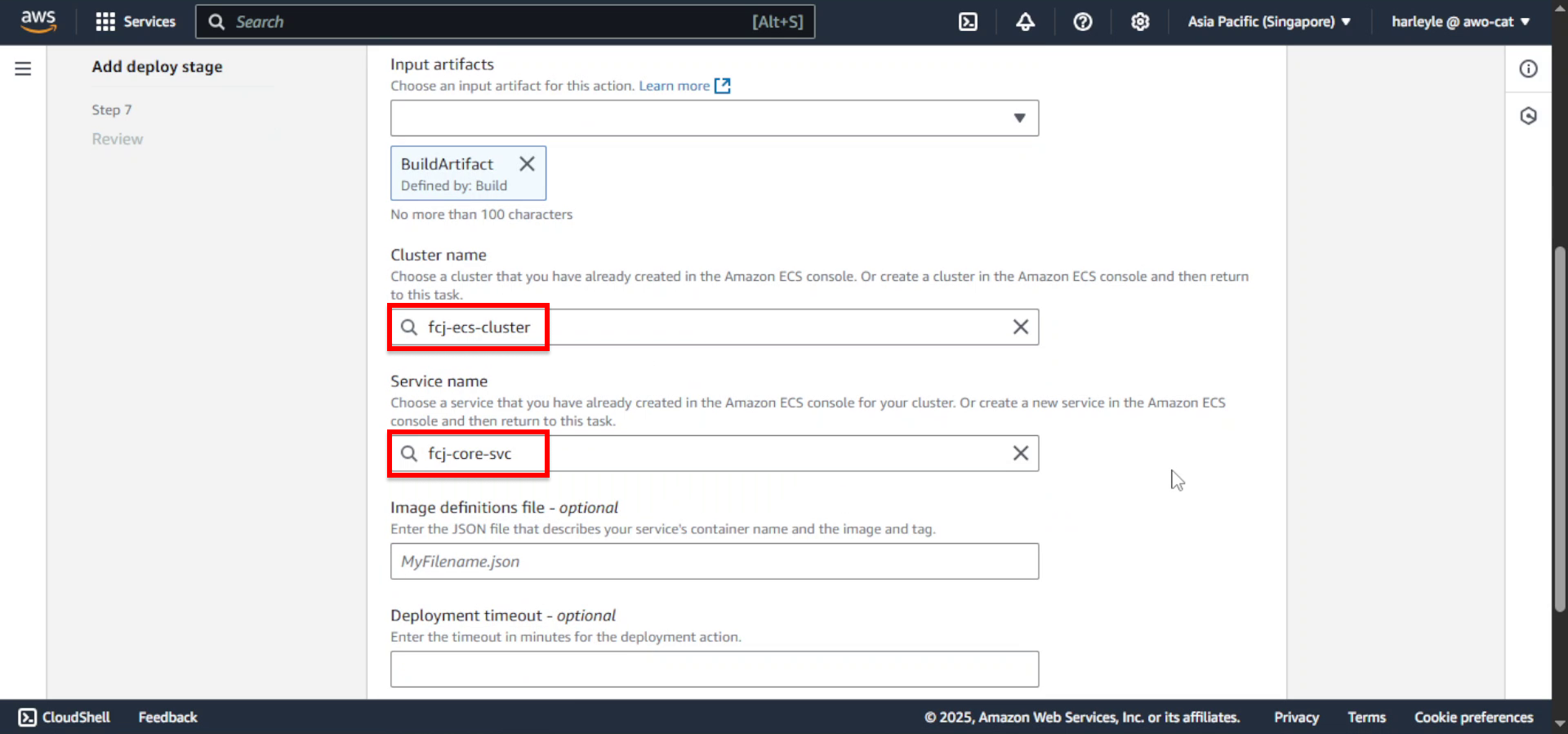
26. Click Next.
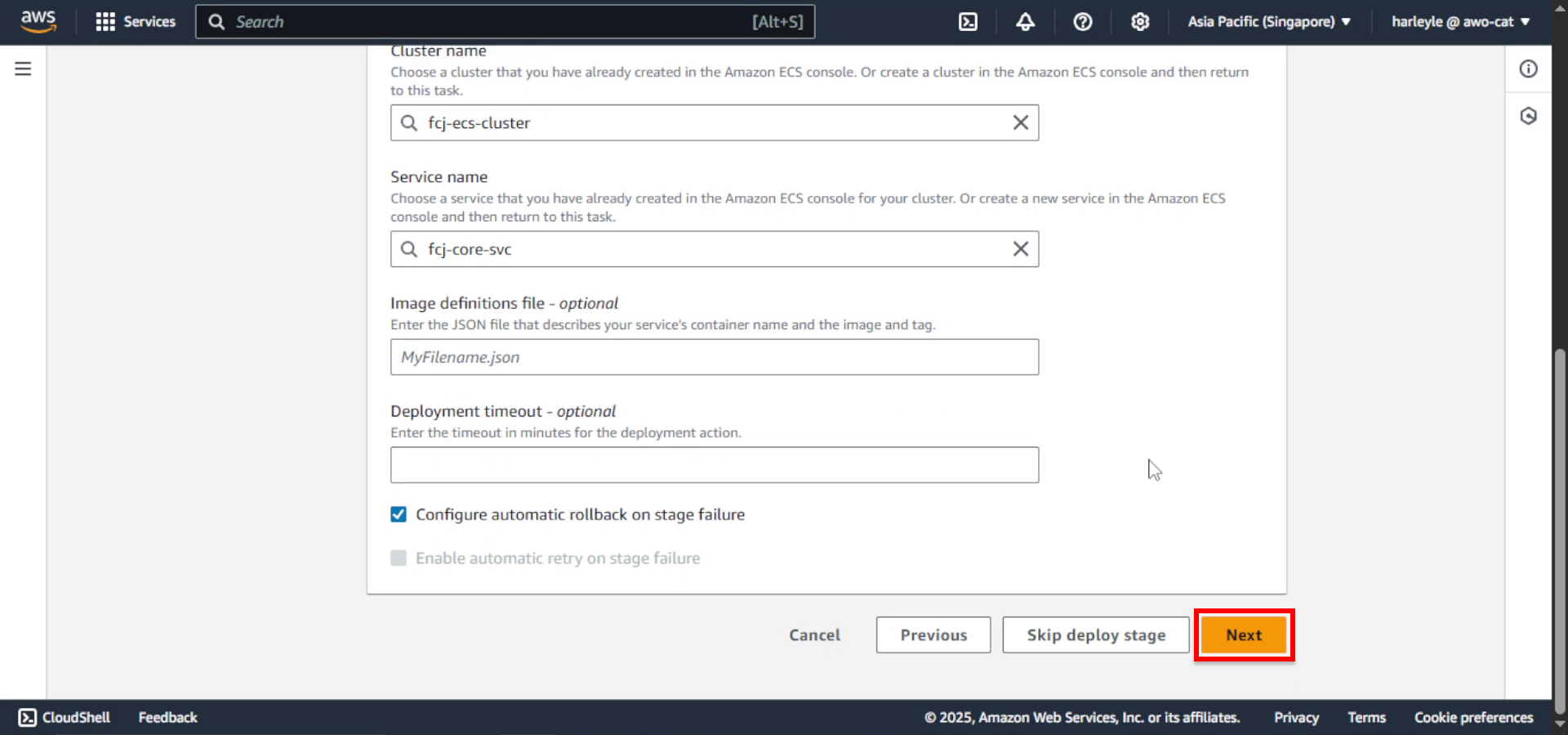
27. Review your configuration and click Create pipeline.
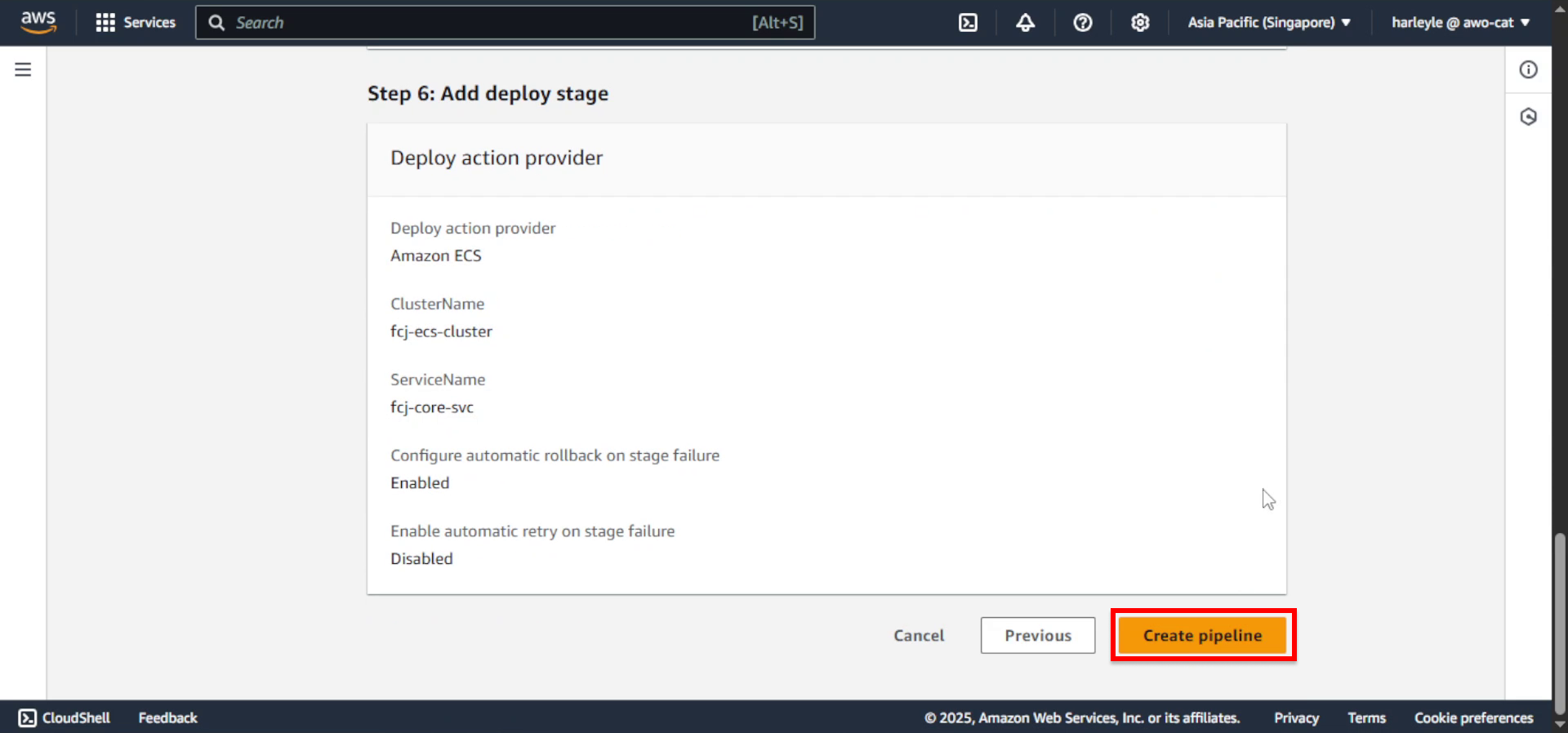
28. Wait for the pipeline to be created. The build stage will fail initially because the CodeBuild service role lacks permissions to access AWS Secrets Manager and Amazon ECR. We will configure the role and rerun the build stage in the next chapter.